
Top Cyber Threats Businesses Will Face in 2026 — And How to Defend Against Them
Top Cyber Threats Businesses Will Face in 2026 — And How to Defend Against Them
Introduction: 2026 Is Not Just Another Cybersecurity Year
Cybersecurity in 2026 will not be an extension of 2025.
It will be a breaking point.
The convergence of artificial intelligence, remote work, cloud dependency, geopolitical cyber warfare, and criminal automation has created a threat environment where every business is a target, regardless of size or industry.
In 2026:
- Attacks will be faster
- Breaches will be harder to detect
- Threat actors will look more legitimate
- And response windows will shrink from days… to minutes
The idea that “we’re too small to be attacked” will finally die.
This article breaks down the top cyber threats businesses will face in 2026, why they are more dangerous than ever, and exactly how organizations must defend themselves to survive and scale.
ALSO, READ Small Business Guide to Cyber Incident Response & Recovery
The 2026 Cyber Threat Landscape: What’s Changed
Before diving into individual threats, it’s critical to understand what fundamentally changed:
- AI has lowered the skill barrier for attackers
- Cloud environments have expanded attack surfaces
- Employees are now the weakest and strongest security link
- Cybercrime has become a business, not a hobby
- Trust-based systems are being actively exploited
Cyber threats in 2026 are no longer noisy or obvious.
They are quiet, patient, and intelligent.
1. AI-Powered Phishing & Social Engineering Attacks
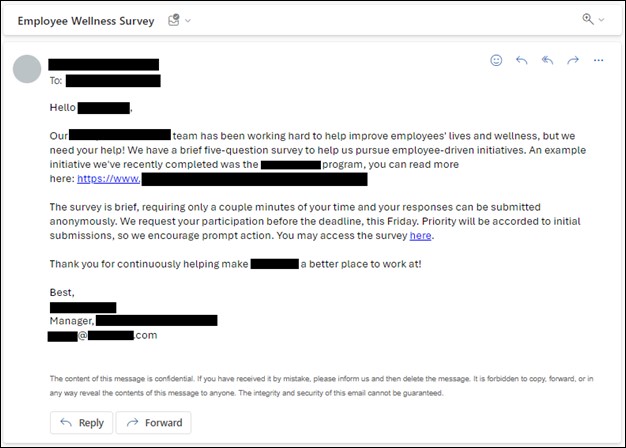

Why This Threat Explodes in 2026
Traditional phishing relied on poor grammar and obvious red flags.
That era is over.
In 2026, attackers use:
- AI-written emails that match tone, role, and context
- Deepfake voice calls impersonating executives
- Real-time data scraped from LinkedIn and company websites
- Personalized lures based on current projects
A finance officer no longer receives a generic email.
They receive:
“Hi Sarah, this is Mark. I’m in a board meeting—can you urgently process the vendor payment we discussed yesterday?”
The voice sounds right.
The timing is right.
The context is perfect.
Business Impact
- Unauthorized wire transfers
- Credential theft
- Cloud account takeovers
- Regulatory exposure
- Reputational damage
How to Defend in 2026
- Mandatory security awareness training focused on AI scams
- Out-of-band verification for all payment or access requests
- Email security with behavioral analysis
- MFA on every business-critical system
- Clear “no exception” payment policies—even for executives
ALSO, READ 2026 Social Media Strategy: What’s Working on TikTok, YouTube, Instagram & X
2. Ransomware-as-a-Service (RaaS) Goes Fully Corporate

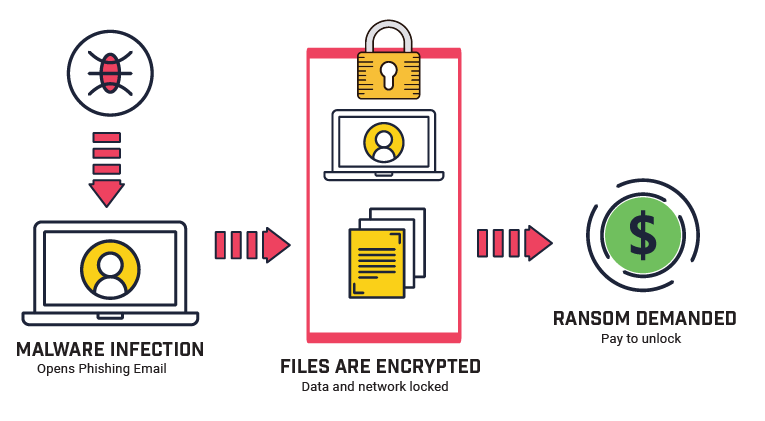
4
Why Ransomware Is Worse Than Ever
Ransomware groups now operate like startups:
- Customer support portals
- Negotiation teams
- Affiliate programs
- Data-leak marketing strategies
In 2026, ransomware is no longer just encryption—it’s extortion + disruption + reputation warfare.
Attackers:
- Steal data first
- Threaten public leaks
- Target backups
- Pressure customers and partners
Business Impact
- Total operational shutdown
- Public exposure of sensitive data
- Legal and compliance penalties
- Long-term trust erosion
- Insurance denial due to poor controls
How to Defend in 2026
- Zero Trust network segmentation
- Immutable, offline backups
- Endpoint Detection & Response (EDR)
- Regular incident response simulations
- Vendor risk assessments
Security platforms from companies like CrowdStrike and Microsoft are increasingly essential—but only when configured properly.
3. Cloud Misconfigurations & Identity Exploits


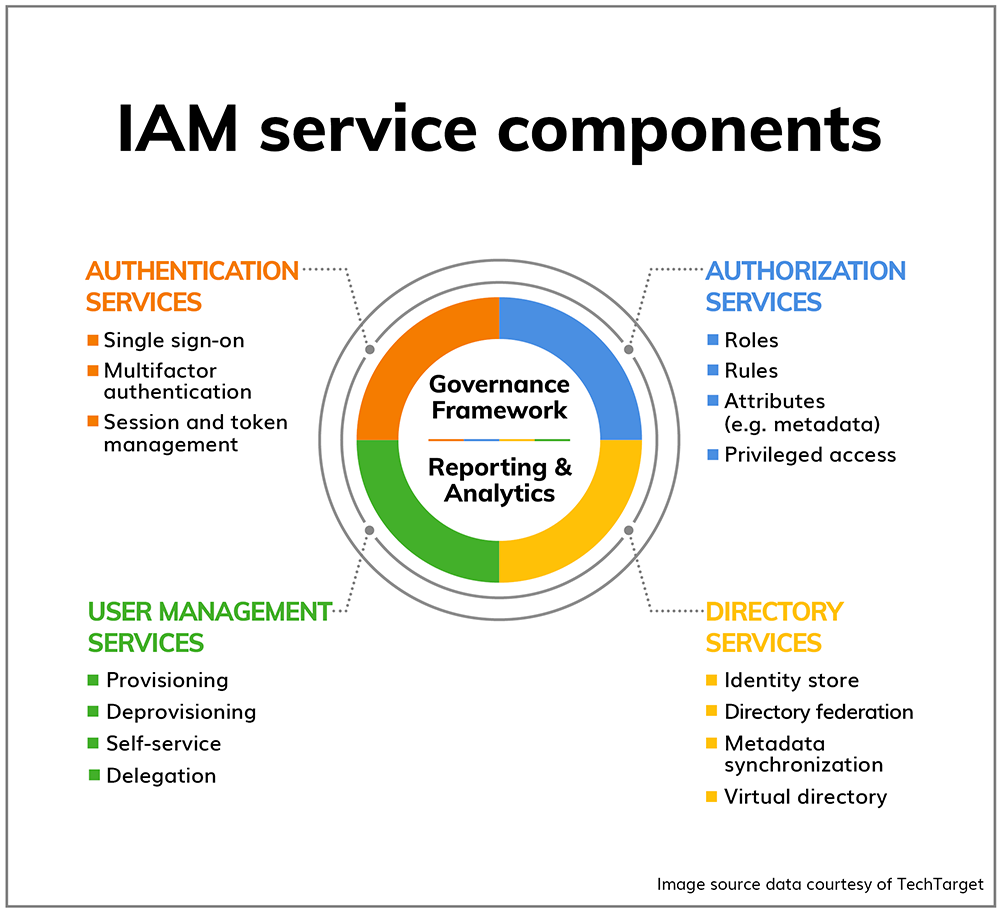
4
The Silent Killer of 2026
Most breaches in 2026 will not come from malware.
They will come from misconfigured cloud resources.
Common issues:
- Public storage buckets
- Over-permissioned IAM roles
- Unmonitored API access
- Stale service accounts
Attackers don’t hack clouds.
They log in.
Business Impact
- Massive data exposure
- Compliance violations (GDPR, ISO, SOC 2)
- Long-term forensic uncertainty
- Customer lawsuits
How to Defend in 2026
- Principle of least privilege
- Continuous cloud security posture monitoring
- Identity-first security strategies
- Regular permission audits
- Strong logging and alerting
Cloud security failures are process failures, not tool failures.
4. Supply Chain & Third-Party Attacks

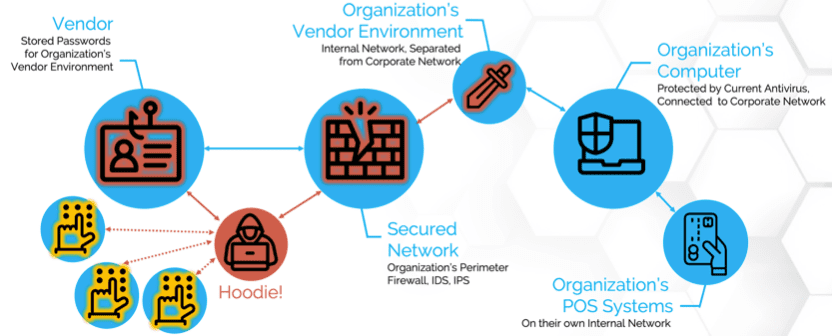
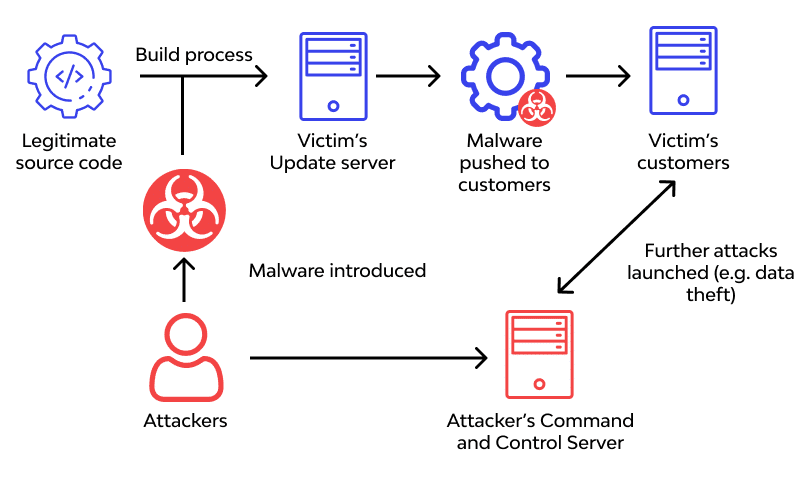
4
Why This Threat Is So Dangerous
In 2026, attackers increasingly avoid hardened targets.
Instead, they:
- Breach a vendor
- Inject malicious updates
- Abuse trusted access paths
- Move laterally into customers
If your vendor is compromised, you are compromised.
Business Impact
- Breaches without direct fault
- Difficult attribution
- Long detection times
- Contractual and legal exposure
How to Defend in 2026
- Vendor risk management programs
- Access segmentation for third parties
- Continuous monitoring, not annual audits
- Software bill of materials (SBOM)
- Incident response coordination with vendors
5. Insider Threats (Malicious & Negligent)



4
The Human Risk Businesses Ignore
Not all insiders are malicious.
Many are:
- Burned out
- Untrained
- Over-privileged
- Unaware of risk
In 2026, hybrid work increases:
- Data leakage
- Credential sharing
- Shadow IT usage
Business Impact
- Intellectual property loss
- Compliance failures
- Data sabotage
- Undetected breaches
How to Defend in 2026
- Privileged access management (PAM)
- Behavioral analytics
- Clear offboarding processes
- Security culture, not fear
- Continuous monitoring of sensitive actions
6. AI Model & Automation Abuse

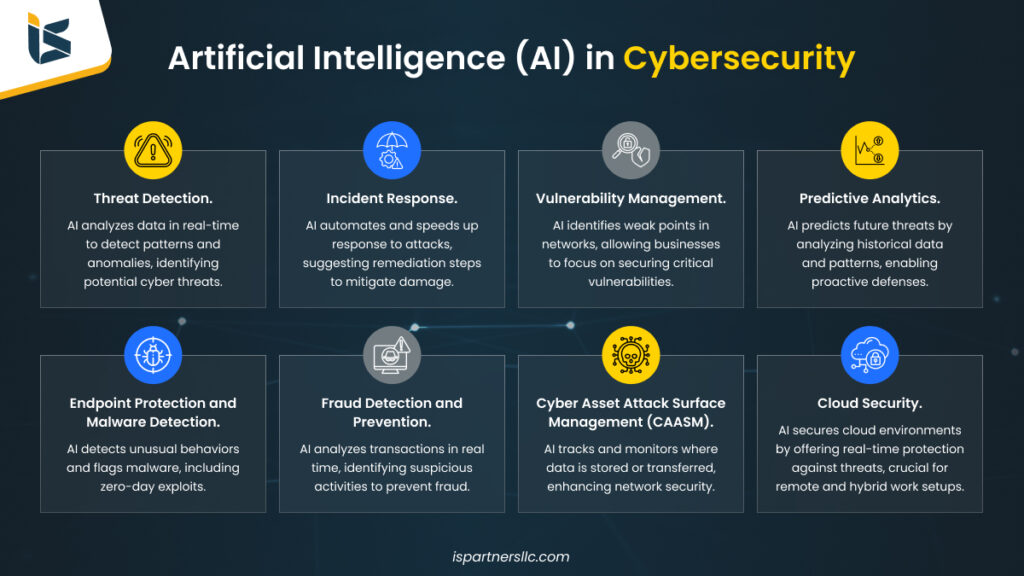
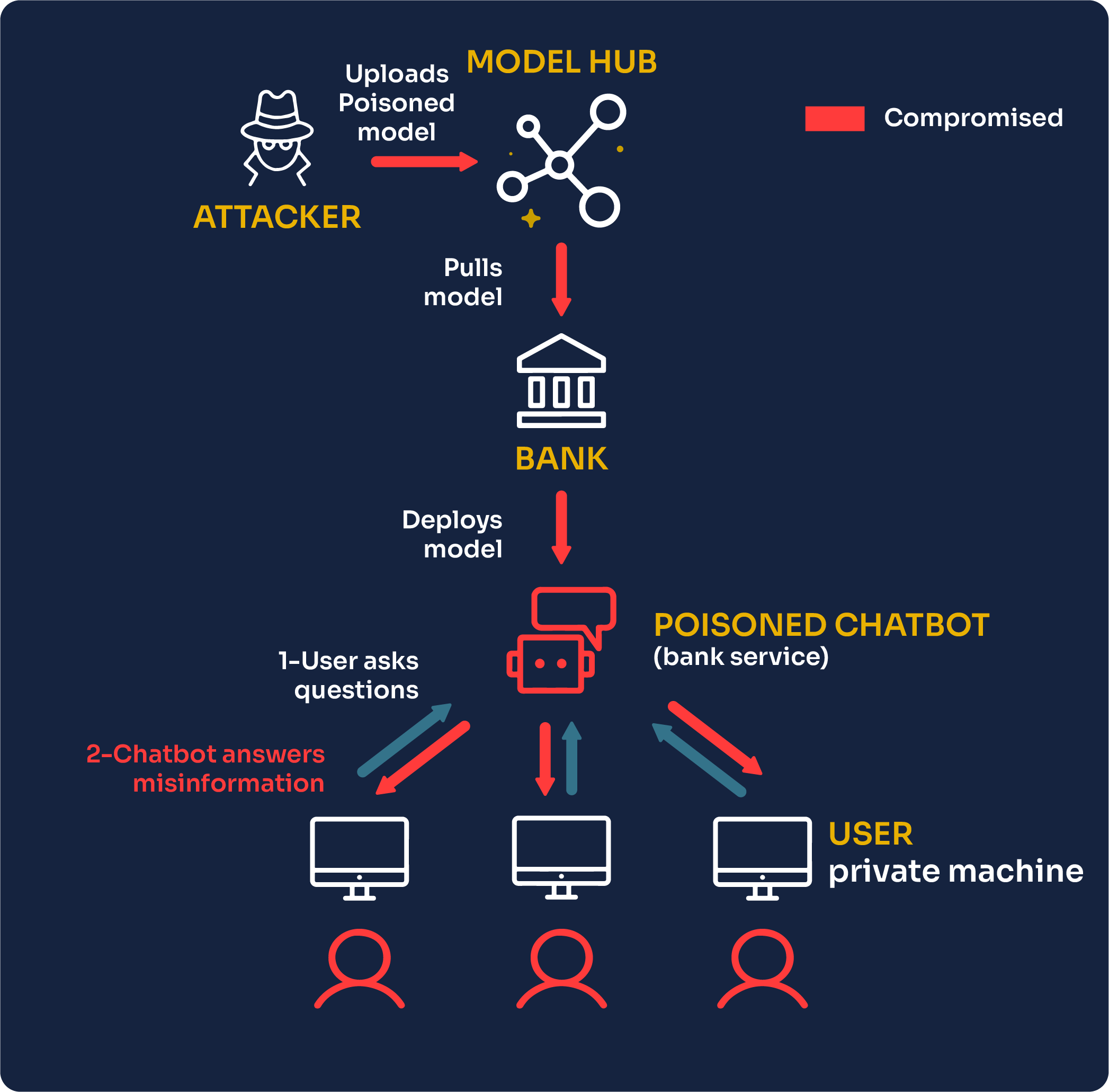
4
A New Category of Risk
Businesses adopting AI tools face new threats:
- Prompt injection attacks
- Data poisoning
- AI output manipulation
- Leakage of sensitive training data
Attackers exploit AI systems because:
- Security controls lag adoption
- Logs are often incomplete
- Trust in AI outputs is dangerously high
Business Impact
- Corrupted decision-making
- Leaked proprietary data
- Legal exposure
- Operational errors
How to Defend in 2026
- AI governance frameworks
- Restricted training data
- Continuous testing and monitoring
- Human-in-the-loop validation
- Clear AI usage policies
7. Regulatory & Compliance-Driven Attacks
The Hidden Cyber Threat
Attackers now exploit:
- Poor logging
- Weak audit trails
- Non-compliance gaps
They know regulatory pressure multiplies damage.
In 2026, a breach is not just technical—it’s legal warfare.
Business Impact
- Heavy fines
- Loss of certifications
- Contract termination
- Executive accountability
How to Defend in 2026
- GRC-aligned security programs
- Evidence-based controls
- Regular compliance assessments
- Clear documentation
- Board-level cybersecurity visibility
The 2026 Cyber Defense Blueprint (What Actually Works)
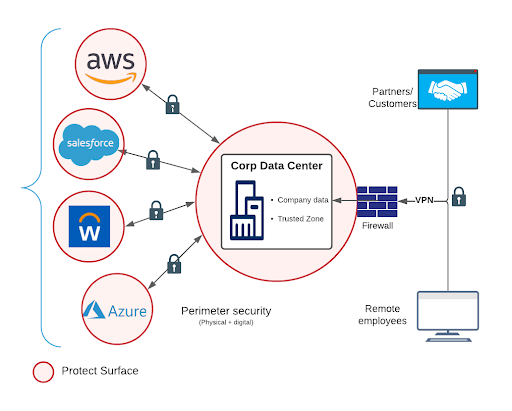


4
To survive 2026, businesses must shift from tool-based security to strategy-based security.
Core Pillars
- Identity-first security
- Zero Trust architecture
- Continuous monitoring
- Employee education
- Incident response readiness
- Governance, Risk & Compliance alignment
Cybersecurity is no longer an IT problem.
It is a business survival strategy.
Final Conclusion: 2026 Will Punish Complacency
The businesses that fail in 2026 won’t fail because they lacked tools.
They will fail because they:
- Underestimated modern threats
- Ignored identity risks
- Delayed security investment
- Treated cybersecurity as optional
Cyber threats in 2026 are inevitable.
Catastrophic damage is not.
The winners will be organizations that prepare now—
before attackers force the lesson.
FAQ
What are the top cyber threats businesses will face in 2026?
The top cyber threats in 2026 include AI-powered phishing, ransomware-as-a-service, cloud misconfigurations, supply chain attacks, insider threats, and AI system abuse.
Why are cyber attacks becoming more dangerous in 2026?
Cyber attacks are more dangerous because attackers now use AI, automation, and stolen identity data to bypass traditional defenses, making attacks faster, stealthier, and harder to detect.
How can businesses protect themselves from ransomware in 2026?
Businesses can defend against ransomware by implementing zero trust security, immutable backups, endpoint detection, employee training, and tested incident response plans.
What role does AI play in cyber threats?
AI enables attackers to automate phishing, impersonate executives using deepfakes, evade detection systems, and scale attacks faster than ever before.
Are small businesses at risk of cyber attacks in 2026?
Yes. Small and mid-sized businesses are prime targets because attackers assume weaker security controls and limited incident response capabilities.



